- Last updated
- Save as PDF
Note
If your organization isusing the Portfolio Financials and Capital Planning products in Procore, you will need to reach out to your Procore point of contact or theSupport team to set up your Azure AD SSO.
You will need to provide the following information when requesting the setup: Single Sign On Issuer URL, Single Sign On Target URL (Optional for IdP-Initiated SSO), and Single Sign On x509 Certificate.
Objective
To configureSP-initiatedSingle Sign-On (SSO)for Procorein Microsoft Azure Active Directory (Azure AD).
Background
To assist you with understanding the terms discussedbelow, here are some definitions:
- Identity Provider (IdP).This is the servicethat verifies the identity of your end users (e.g., Okta, OneLogin, or Microsoft Azure AD).
- Issuer URL (Entity ID).A unique string that identifies theproviderissuing a SAML request.
- SAML. Short for Security Assertion Markup Language.
- Service Provider (SP).Procore
- Target URL.The IdP URL that will receive SAML requests from Procore.
- X.509Certificate. This is an encrypted digital certificatethat contains the required values that allow the SSO service toverify the identities of your users.
If your company wants to use Azure AD SSO to manage user logins to Procore, these configurations are supported:
- Service Provider Initiated (SP-initiated) SSO. Referred toas Procore-initiated SSO, thisoption gives your end users the ability to sign into the Procore Login page and then sends an authorization request to the IdP. Once the IdP authenticates the user's identify, the user is logged into Procore.To configure this solution with Microsoft Azure AD, seethe Steps below.
OR - Identity Provider Initiated (IdP-initiated) SSO. With this option, your end users must log into your Identity Provider's SSO page (for example, Azure AD)and then click an icon to log into and open the Procore web application. To configure this solution, see Configure IdP-Initiated SSO for Microsoft Azure AD.
Things to Consider
- Required Permissions:
- Global Administrator rightsto Azure AD.
AND - 'Admin' level permissions to Procore's Company level Admin tool.
- Global Administrator rightsto Azure AD.
- Prerequisites:
- Complete all the Preparation Phasesteps outlined in Setup Guide: Microsoft Azure AD.
- Supported Azure AD Editions:
- Microsoft Azure Active Directory
- Supported Authentication Protocol:
- Security Assertion Markup Language (SAML 2.0)
- Additional Information:
- What is Single Sign-On (SSO)?
- How do I set up Single Sign-On (SSO) with Procore?
- Which SSO identity providers are supported by Procore?
- Do Procore's SSO integrations support single or multiple domains?
Steps
- Step 1: Add Procoreas a New Enterprise Application in Azure AD
- Step 2: Configure the Procore Enterprise Application's SSO Settings
- Step 3:Add the Azure AD Settings to Procore'sCompany Level Admin Tool
Step 1: Add Procore as a New Enterprise Application in Azure AD
- Log in to the Azure AD portal as a Global Administrator: http://portal.azure.com

- Under Favorites, clickAzure Active Directory.
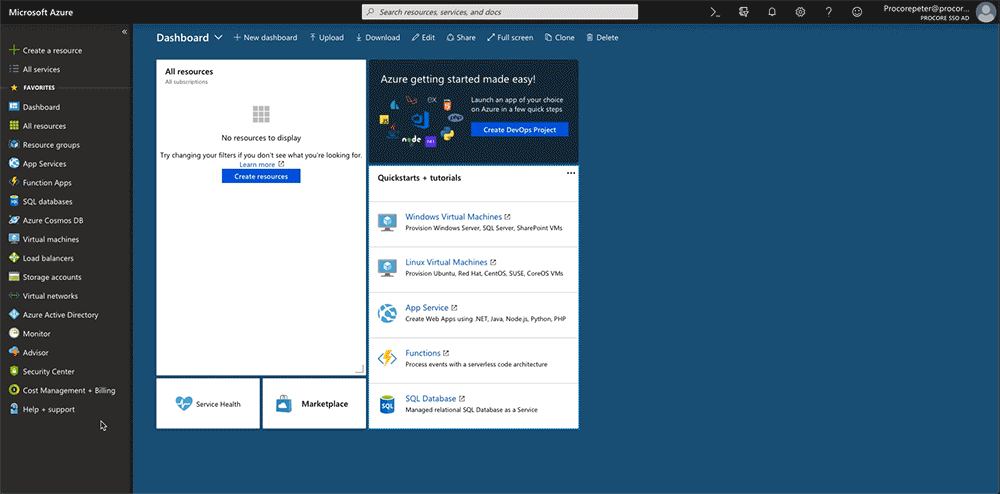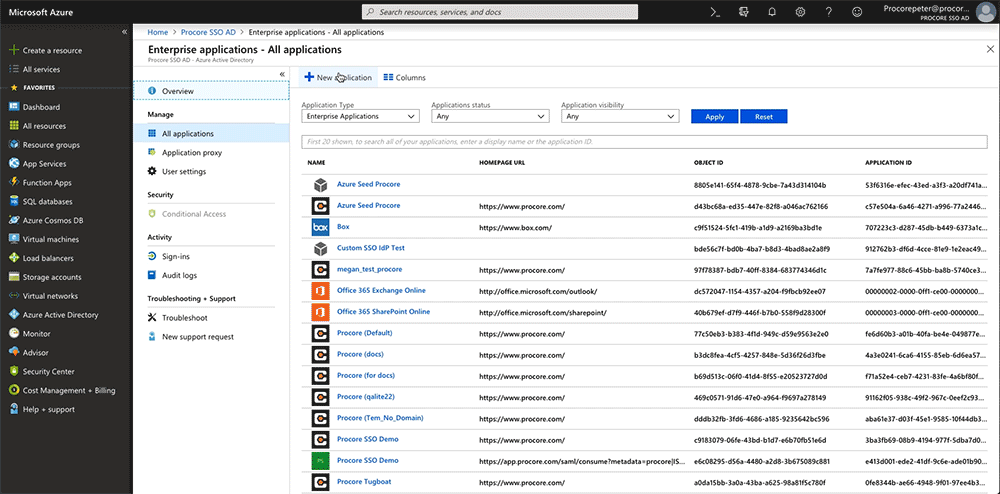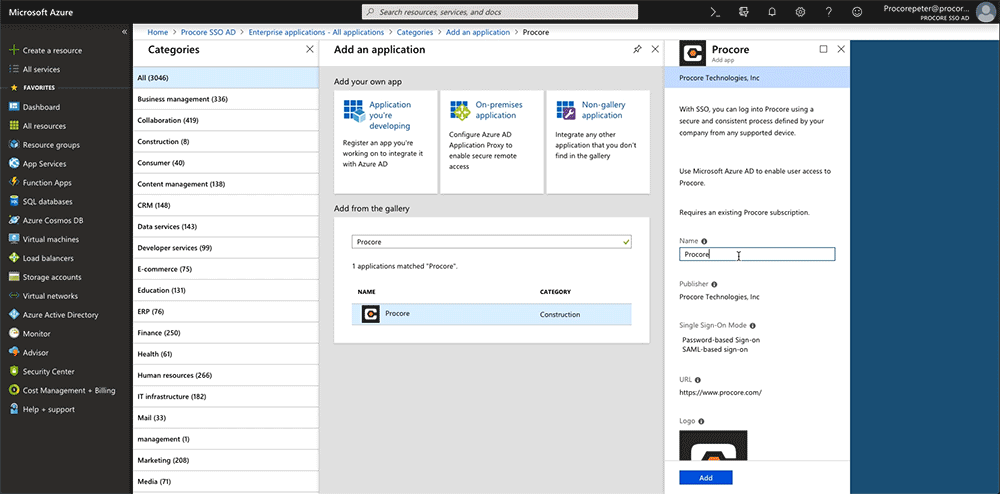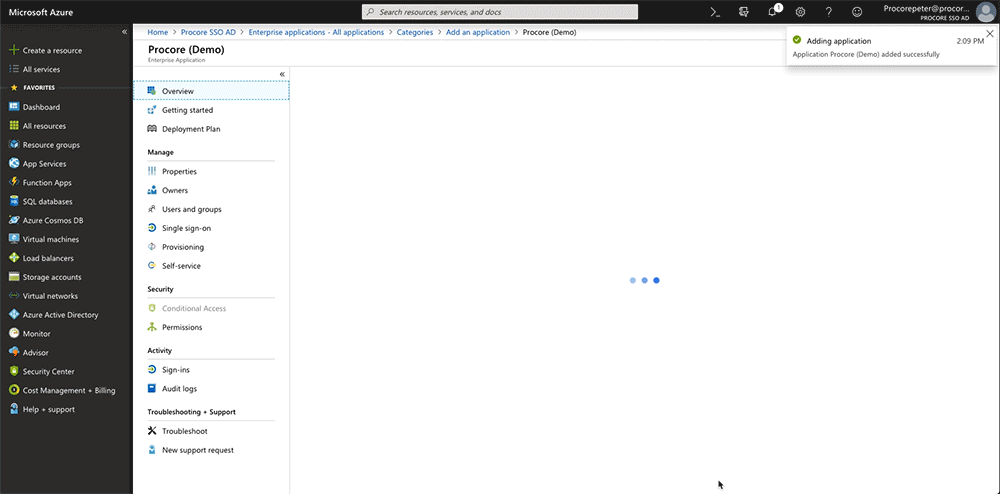
- Under Manage, click Enterprise Applications.
- Click +New Application.
- Under Add from the Gallery, type the following in the Enter a Name box: Procore
- Click the matching application namedProcore.
This reveals a new pane. - In the Name box, typea name for your application.
Note: In the example above, we named our application: Procore (Demo) - ClickAdd.
A message appears to confirm that the application was added successfully. You should now be viewing your newProcoreenterprise application'sOverview page.
Step 2: Configure the ProcoreEnterprise Application's SSO Settings
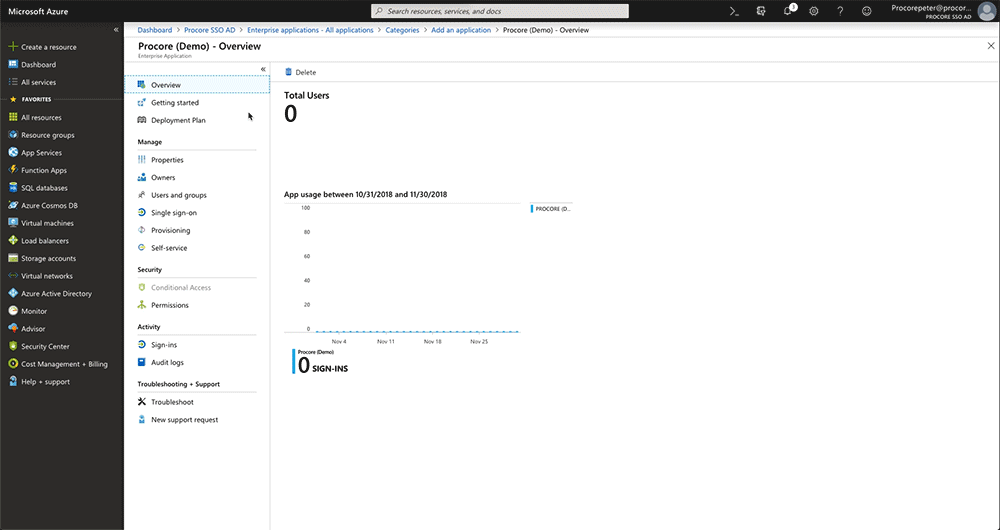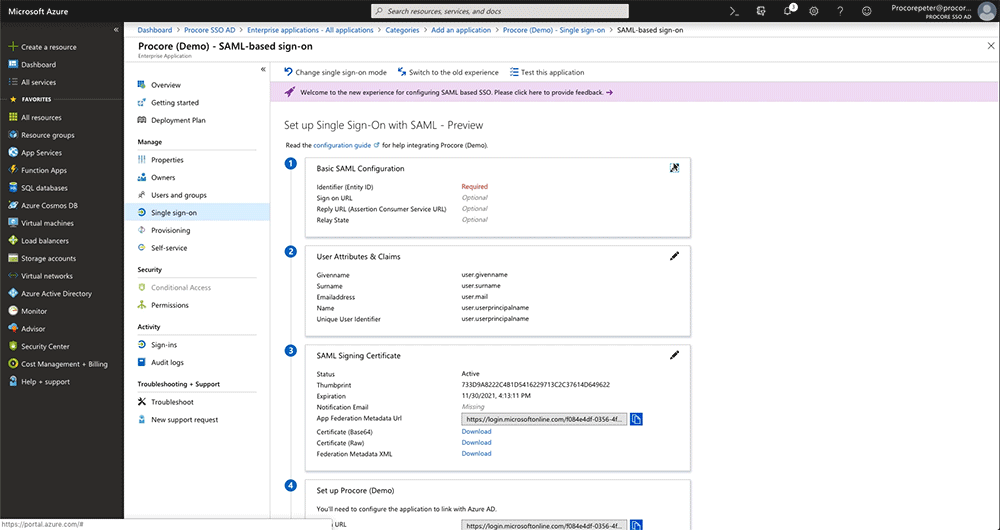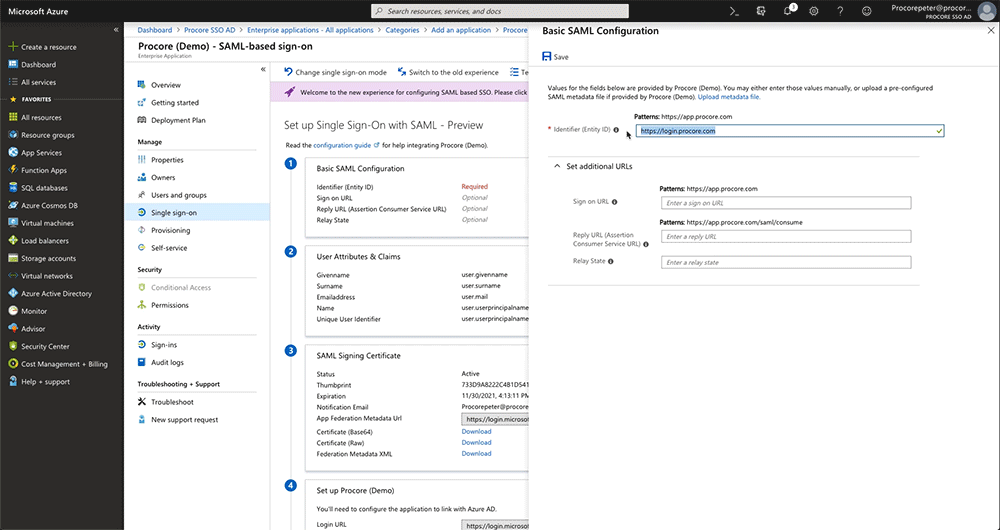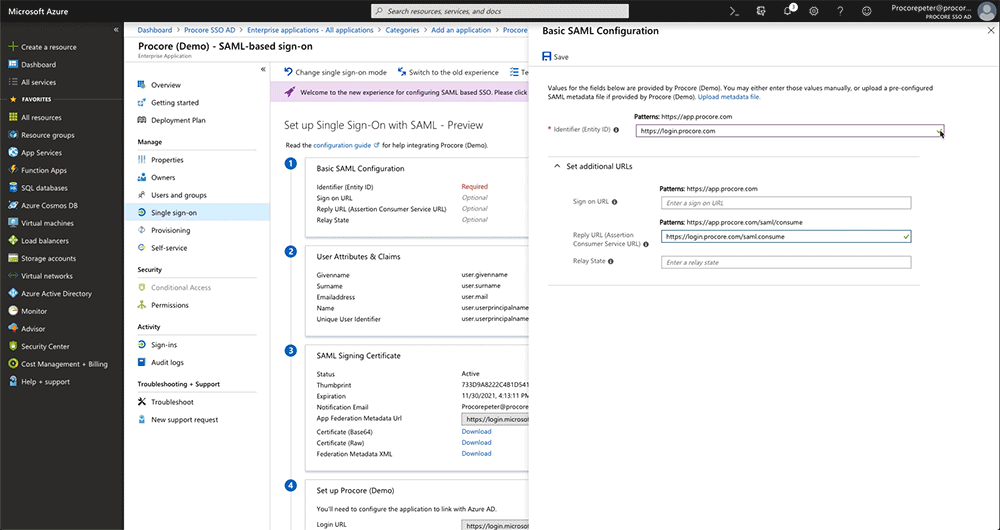
- In the Overview page for your new enterprise application, under Manage, click Single Sign-On.

- In the Single Sign-on Modepage, click SAML.
This opens theSet Up Single Sign-On with SAML- Preview page. - Under Basic SAML Configuration, clickEdit.
This opens the Basic SAML Configuration window. - Under the Basic SAML Configuration page, do the following:
- Identifier (Entity ID)
Change the value from:https://app.procore.comto:https://login.procore.com
Note:If you are using Portfolio Financials and Capital Planning, enter the following value instead:https://www.honestbuildings.com/pfcp/app/#!/login
Optional - Unique Entity ID
When configuring SSO for a singleProcore instance, you should NOT check this box.
If your company licensesmore than one Procore instance, and you wantto configure unique Procore enterprise applications within your IdP tenant for each instance, you can by enablingUnique Entity ID. If enabled, youare still limited to one (1) enterprise application per Procore company instance.
Important:SSO for Procore targets users by email domain.An email domain can only be targeted once in all of Procore, so if you're considering setting upSSO with Unique Entity IDs acrossmultiple Procore instances, remember that you can only target an email domain once, in a singleinstance.
To generate a Unique Entity ID for an enterprise application, check theEnableUnique Entity IDbox in the Procore Admin tool's SSOconfiguration page for the Procoreinstance you want to specify on anenterprise application. Checking this boxwill generate a uniqueEntity ID URL in the field below, which you will then copy and paste into theappropriate Entity ID field in your IdP'sconfiguration page.
Notes: You must save your configuration with the box checked to generate the Unique Entity ID. Enabling this feature does not impact user membership or access to a given instance. Access to a company in Procore is determined by a user's presence in the Directory tool, and their configured permissions within Procore. Auto-provisioning with SSO is not supported at this time.

- Sign On URL
Leave this field blank. You do NOT need to enter a value in this field. - Reply URL (Assertion Consumer ServiceURL)
Enter the following:https://login.procore.com/saml/consume
- Identifier (Entity ID)
- Click Save.
A message appears to confirm that your settings were saved successfully. - Click the 'x' to closethe Basic SAML Configurationpage.
- UnderSAML Signing Certificate, click the Download link for the Certificate (Base64) file.
Notes:- This downloads a file named PublicCertificate.cer to your browser's specified download area.
- Open the file in a text editor and leave it open on your computer. Later, you will copy the code that appears between the ---BEGIN CERTIFICATE--- and ---END CERTIFICATE-- tags into Procore.

Step 3: Add the Azure AD Settings to Procore'sCompany Level Admin Tool
- Leave the Azure AD page open as described in the previous step.
- Log into Procoreusing your Procore Administrator account.
- Navigate to the Company levelAdmintool.
- UnderCompany Settings, clickSingle Sign On Configuration.
- Leave Procore's'Single Sign On Configuration' page open.
- Go to the Azure AD page that you left open.
- Under Set Up [Your Application Name], click View Step-by-Step Instructions.
This opens the Configure Sign-On page.
Copy this information from Azure AD… Paste it into this field in Procore… SAML Entity ID
Copy the URL in this field from Azure AD.Single Sign On Issuer URL
Paste the SAMLEntity IDURL into the Single Sign On Issuer URL field.

SAML Single Sign-On Service URL
Copy the URL in this field from Azure AD.Single Sign On Target URL
Paste the SAML Single Sign-On ServiceURL into the Single Sign On Target URLfield.

SAML XML Metadata
Download this file to your computer and open it in a text editor (i.e., Notepad or Text/Edit). Locate the certificate data that appears between the HTML start and end tags for the x509 certificate. Then copy the data. Do NOT copy the tags. This isdepicted in the animated image above:Start Tag: <X509Data><X509Certificate>
End Tag: </X509Data></X509Certificate>
Single Sign On x509 Certificate
Paste the certificate data you copied into this field.

- On the 'Single Sign On Configuration' page in Procore, click Save Changes.
- Reach out to Procore Support or your company'sProcore point of contact to requestthey configure the email domain(s) you'd like to target for SSO.
- After you receive confirmation that the SSOconfiguration is ready, mark the Enable Single Sign On checkbox on the 'Single Sign On Configuration' page.
- Select the Service Provider Forward option.
- Click Save Changes.
See Also
- Log into Procore-Initiated SSO for Microsoft Azure AD